 Another year, another DEFCON!
Another year, another DEFCON!
What did DEFCON 27 have in store for us?
This being our 16th DEFCON, we’ve been around the block a few times. Here at HackRepair.com, we strive to stay ahead of the curve and stay on top of the latest trends in information security, attack vectors, mitigation, and incident response.
Join us as we take a stroll through this years DEFCON hacking convention, and learn a few new things along the way.
Quite a few pictures below, so be sure to click each to enlarge.
Our top 10 favorite talks from DEFCON 27!
In no particular order:
- “Are Quantum Computers Really A Threat To Cryptography? A Practical Overview Of Current State-Of-The-Art Techniques With Some Interesting Surprises”
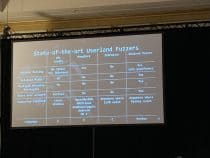
- “Zero bugs found? Hold my Beer AFL! How To Improve Coverage-Guided Fuzzing and Find New 0days in Tough Targets”
- “Behind the Scenes: The Industry of Social Media Manipulation Driven by Malware”
- “Evil eBPF In-Depth: Practical Abuses of an In-Kernel Bytecode Runtime”
- “API-Induced SSRF: How Apple Pay Scattered Vulnerabilities Across the Web”
- “100 Seconds of Solitude: Defeating Cisco Trust Anchor With FPGA Bitstream Shenanigans”
- “Tales From the VoIP Support Desk”
- “State of DNS Rebinding – Attack & Prevention Techniques and the Singularity of Origin”
- “Go NULL Yourself or: How I Learned to Start Worrying While Getting Fined for Other’s Auto Infractions”
- “HTTP Desync Attacks: Smashing into the Cell Next Door”
What the heck is SSRF, or how to pwn Apply Pay for websites?
Vendor-specific payment gateways are pretty ubiquitous these days, what with Google Pay, Amazon Pay, and Apple Pay dominating, and 2 of them having built-in functionality on hundreds of millions of mobile devices around the world.
In “API-Induced SSRF: How Apple Pay Scattered Vulnerabilities Across the Web”, the issue of the day is with Apple Pay, and their use of close to 20 validation domains. Because of this, their previously recommended validation check documentation and example code has unleashed dozens of vulnerable websites across the web. Nearly all of them vulnerable to Server Side Request Forgery, due to incomplete or completely lacking verification of HMAC Signatures, and lax security policies on local hosts, allowing a remote attacker to access local files and network resources.
Coming back for a bit more SSRF goodness is “Owning The Cloud Through Server-Side Request Forgery”, with its use of unsanitized user inputs to exfiltrate data from many top transportation, hospitality, and social media platforms utilizing the cloud.
Villages, Villages, Everywhere!
DEFCON has been expanding at a near exponential rate for several years now. Every time I go, there’s something new, or an expanded venue for existing villages. This year saw the return of the Voting Machine Village, ICS Village, Car Hacking Village, Hardware Hacking Village, Wireless Village, etc. And the addition or expansion of such things as the Hack The Sea Village, Blue Team Village, Dronewarz village, Biohacking Village, Social Engineering Village, and many others.
#BADGELIFE — Or how to blow thousands of dollars for a shiny
#BADGELIFE is now in its 2nd or 3rd year, depending on how you look at it. The vast proliferation of inexpensive PCB manufacturing (GO PURPLE! Oshpark!), easy cad-based PCB design, cheap parts, and inexpensive pick&place & reflow ovens has caused unique, interesting, and downright fascinating electronic badge designs to proliferate throughout DEFCON and every other information security conference on the planet. Whereas last year there was somewhere around ~200 different custom badges around the conference, including the SAO (S**tty Add-On) and full-scale badges with wireless mesh networking and gorgeous color LCD screens… with the majority being basic 1-2 LED affairs, we now have as many custom PCBs encompassing every imaginable form, function, and purpose. An informal list can be found here.
Many of the high-end badges run from $100-$150/ea and some are even given away for free based on the help of sponsors, donors, or just plain charity of excited hardware developers.
Here’s a few of my favorites, as well as a link to Joe Grand’s DEFCON 27 badge discussion.
The Future is Quantum. Cryptography that is…. PS: Crypto Means Cryptography
A fun, interesting, and downright scary talk delved into the status of Quantum Computing, and the threat of Quantum Computers’ capability to decrypt most known methods of cryptography in use today. Here Are Quantum Computers Really A Threat To Cryptography? A Practical Overview Of Current State-Of-The-Art Techniques With Some Interesting Surprises dives into the very real world of Quantum Computer and discusses the basis of current efforts to break modern cryptography, Shor’s Algorithm.
Through many many revisions of the algorithm, and the advancement of Quantum hardware, known as Qubits, to encompass true Quantum machines comprised of many hundreds of Qubits, as well as the development of adiabatic Quantum computers such as D-Wave, the current timeline for breaking a 128bit RSA key is now less than 10 years. This means that cryptography that was considered completely secure just a few short years ago is now entirely worthless, with jumps to 256bit, 1024bit, and 2048bit failures in the near future as advancements in algorithms and software/hardware technology in the Quantum Computer sector continue to outpace the development of Post-quantum cryptography.
With DEFCON 27, Las Vegas behind us, we are still digesting all of the wonderful security tips and recommendations.
We’ll see you next year, at the brand new Caesar’s Forum for DEFCON 28.
This will be the first departure of the conference in its history from a Hotel/Casino, to a full-on convention center venue, within the 2 largest pillar-less ballrooms in the entire world. Until then, stay secure!
“Secure By Default” is our philosophy and this is how we do it.
























Leave a Reply