 Here we are, another DEFCON in the books, DEFCON 26!
Here we are, another DEFCON in the books, DEFCON 26!
We’ve been going to DEFCON officially and unofficially for many years now (15 to be exact!), and though it keeps getting bigger, we are here every year to learn about the latest in information security, hacking, mitigation, and hear from real people wearing all shades of hats. All of this, to keep you, your sites, and your companies secure, and to help clean up when the worst happens.
While we have no definitive list of top talks, here are some of our 10 favorites from this year.
In no particular order:
- Playback: a TLS 1.3 story
- GOD MODE UNLOCKED: Hardware Backdoors in [redacted] x86 CPUs
- Weaponizing Unicode: Homographs Beyond IDNs
- I’ll See Your Missile and Raise You A MIRV: An overview of the Genesis Scripting Engine
- Reaping and breaking keys at scale: when crypto meets big data
- You’d better secure your BLE devices or we’ll kick your butts!
- Detecting Blue Team Research Through Targeted Ads
- Booby Trapping Boxes
- What the Fax!?
About exploits.
There were quite a few exploits and new tools released this year. Including our personal favorite, GScript, authored and presented by the fine folks behind “I’ll See Your Missile and Raise You A MIRV: An overview of the Genesis Scripting Engine”.
This tool, GScript, provides a new method of bundling and executing exploits on remote systems, and is some of the slickest codings we’ve seen come down this pipeline in years. We will certainly be on the lookout for malware utilizing it in the near future, and will be doing research into mitigation for it immediately.
One of the biggest security vulnerabilities released in the last few years is, of course, SPECTRE / MELTDOWN. And now with the release of the ‘FORESHADOW’ vulnerabilities just a few days ago, we are presented with an ever larger threat of legitimate CPU compromises across all business sectors.
The talk “GOD MODE UNLOCKED: Hardware Backdoors in [redacted] x86 CPUs” was a deep-dive discussion of the possibilities of legitimate hardware backdoors in processors. Leading to absolutely undetectable entry points to all computers.
Questions of the day:
1. Do you still use FAX machines?
2. Are they connected unencumbered to your corporate, small business, or even home network?
The talk, “What the Fax!?” goes into this little-thought-of device’s brain, and finds quite the interesting story, involving Commander Keen, a mysterious encoding, and today’s corporate world.
Apparently, FAX machine firmware can be upgraded by sending a FAX. This can open your entire network to attackers, and compromise computers and servers on your network just seconds after the FAX with the malware-laden firmware is received.
The style side of things.
#BADGELIFE is the new phenomenon where many different individuals and groups are now creating their own custom badges that do anything from blink a couple LEDs, to play games, transfer images, or even interact wirelessly over large distances. Here’s a great video by HACKADAY that shows off just a small percentage of the great badges this year:
About Public Key Cryptography.
And finally, a discussion on the security of Public Key Cryptography, which has literally been the foundation for modern security for decades.
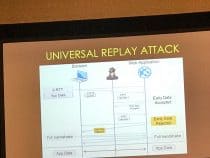
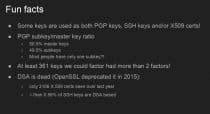
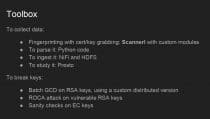
“Reaping and breaking keys at scale: when crypto meets big data” was a talk about one group’s quest to collect all of the publically available keys on the internet. Once they collected enough keys, they could infer the private keys from closely related public keys.
With DEFCON 26, Las Vegas behind us, we are still digesting all of the wonderful security tips and recommendations. We’ll see you next year, back at Paris / Bally’s / Planet Hollywood for DEFCON 27! Enjoy!
“Secure By Default” is our philosophy and this is how we do it.













Leave a Reply