Phishing scams, spear phishing, and social engineering are techniques often used by cybercriminals to gain unauthorized access to data, websites, and other online accounts. These attack types are becoming increasingly common, and understanding them is the first step towards cybersecurity.
Bonus!
While Google is a great place to start in checking to see what personal information about you is available in Google Search, I’ve included a list of opt-out links for a number of people search websites at the end of this article as well.
Links to Key Topics
- 1.0. Understanding the Threats
- 2.0. Top 20 Related Terms and Description of Each
- 3.0. Google’s Role in Cybersecurity
- 4.0. Protecting Yourself from Social Engineering Attacks
- 5.0. Securing Your Personal Information
- 6.0. Opt-Out Links for People Search Websites
- Conclusion
1.0. Understanding the Threats
1.1. Phishing is a fraudulent practice where emails purporting to be from reputable companies are sent to individuals to induce them to reveal personal information, such as passwords and credit card numbers.
1.2. Spear phishing is a more targeted version of this attack, where the cybercriminal has done their research and set their sights on a particular user.
1.3. Social engineering, on the other hand, involves the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes. Social engineers are clever threat actors who use manipulative tactics to trick their victims into performing a desired action or disclosing private information.
2.0. Top 20 Related Terms and Description of Each
- Baiting: A social engineering tactic that uses a false promise to pique a victim’s greed or curiosity.
- Clone Phishing: A type of phishing attack whereby a legitimate, previously delivered email containing an attachment or link has had its content and recipient address(es) taken and used to create an almost identical or cloned email.
- Dumpster Diving: The practice of sifting through trash to find documents that contain sensitive information.
- Honey Trap: A deceptive operation designed to catch a person committing a crime by means of temptation.
- Impersonation: A form of fraud in which an attacker pretends to be another person or entity in order to trick the victim.
- Man-in-the-Middle Attack (MitM): A type of cyber attack where communication between two users is monitored and modified by an unauthorized party.
- Pharming: A cyber attack intended to redirect a website’s traffic to another, fake site.
- Piggybacking: A type of social engineering attack where the attacker gains unauthorized access to a system or network by leveraging a legitimate user’s access privileges.
- Pretexting: A form of social engineering where attackers focus on creating a good pretext, or a fabricated scenario, that they use to try and steal their victims’ personal information.
- Quid Pro Quo: A type of social engineering attack where the attacker requests personal information from the victim in exchange for something desirable.
- Ransomware: A type of malicious software designed to block access to a computer system until a sum of money is paid.
- Scareware: A form of malicious software that uses social engineering to cause shock, anxiety, or the perception of a threat in order to manipulate users into buying unwanted software.
- Shoulder Surfing: The practice of spying on the user of a cash-dispensing machine or other electronic device in order to obtain their personal identification number, password, etc.
- Smishing: A type of phishing attack where text messages are used to trick the victim into giving up sensitive information.
- Spear Phishing: A targeted form of phishing where the attacker has done their research on the victim and tailors their approach accordingly.
- Tailgating: A type of social engineering attack where the attacker gains unauthorized access to a restricted area by following an authorized person.
- Trojan Horse: A type of malware that is often disguised as legitimate software.
- Vishing: A form of phishing that uses voice communication technology, such as phone calls, to trick victims into giving up sensitive information.
- Watering Hole Attack: A security exploit in which the attacker seeks to compromise a specific group of end users by infecting websites that members of the group are known to visit.
- Whaling: A type of phishing attack that specifically targets senior executives and high-profile targets.
3.0. Google’s Role in Cybersecurity
To better prevent both phishing and social engineering attacks, Google has recently begun a campaign to better manage the “personal data” previously saved in Google Search. Google is offering to help you remove certain types of data from Google Search, including:
 Bank account numbers
Bank account numbers- Credit card numbers
- Images of handwritten signatures
- Images of ID docs
- Highly personal, restricted, and official records, like medical records
- Personal contact info, like physical addresses, phone numbers, email addresses
- Confidential login credentials, and more…
However, it’s important to remember that Google Search is just a search engine and has no relation to the actual websites and data. So removal from search will not take down the websites presenting your data online. Google Search does have a helpful article on how to “Contact a site’s webmaster” as well.
4.0. Protecting Yourself from Social Engineering Attacks
While Google’s efforts are commendable, it’s crucial to take additional steps to protect yourself from social engineering attacks. This includes being aware of the common types of social engineering attacks, such as pretexting, baiting, quid pro quo, tailgating, piggybacking, and the other terms described above. Each of these attacks involves different tactics and requires different preventive measures.
For example, multi-factor authentication can be an effective way to prevent unauthorized access to your accounts, even if your login credentials are compromised. Similarly, being cautious about clicking on web links, especially those in unsolicited emails, can help protect you from phishing and spear phishing attacks.
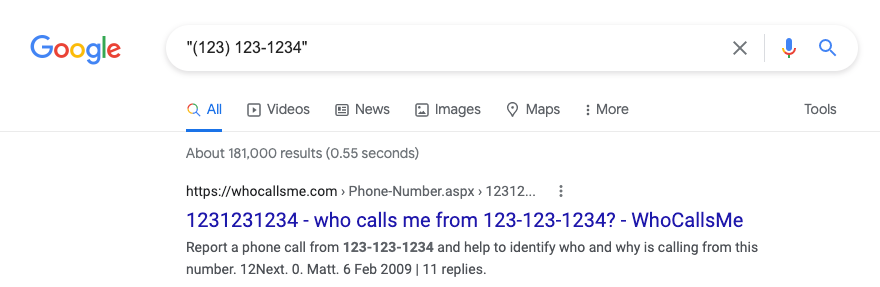
5.0. If you are looking to better secure the information publicly available online, I recommend starting with your personal phone number.
Simply enter your phone number in search like this: “(123) 123-1234”
 If you do see your personal information displaying readily in Google search and would like to remove it, see the article, “A new Search tool to help control your online presence“.
If you do see your personal information displaying readily in Google search and would like to remove it, see the article, “A new Search tool to help control your online presence“.
_
The article linked above to Google’s blog introduces a new tool in Google Search called “Results about you“. This tool allows users to easily request the removal of search results that contain their personal phone number, home address, or email address directly from the Google app or Google Search.
6.0. Opt-Out Links for People Search Websites
As a thank you for reading my article, below are eight ways to start in clearing personal data from popular people search websites as well:
- BeenVerified (Address Search): This page is specifically for opting out of BeenVerified’s address search function.
- BeenVerified (Search): This is an opt-out page for BeenVerified’s search function. You can request the removal of your information from their search results.
- Google: Google provides a troubleshooter page to guide you through the process of removing your personal information from Google Search.
- InstantCheckmate: The InstantCheckmate opt-out page was not accessible at the time of checking. You may need to try again later.
- Intelius: The Intelius opt-out page was not accessible at the time of checking. You may need to try again later.
- MyLife: MyLife is a reputation platform that also provides people search functionality. However, the main page does not provide a direct opt-out link. You may need to contact their customer service for removal requests.
- PeekYou: This page allows you to request that PeekYou does not sell your personal information, in compliance with the California Consumer Privacy Act (CCPA).
- Spokeo: This page allows you to opt-out of Spokeo, a people search engine that aggregates data from online and offline sources. You need to provide the URL of your profile to request removal.
- StateRecords: This page provides information about your privacy rights and offers a form to request the removal of your personal information from their website.
- Whitepages: This page allows you to request the removal of your information from Whitepages, a popular people search website.
Remember, removing your information from these sites does not guarantee it will be removed from the entire internet, as the data might be available on other websites.
Conclusion
The increasing prevalence of phishing scams and social engineering attacks necessitates proactive measures to secure personal information online. Google’s initiative to manage and remove personal data from its search results is a significant step towards enhancing online privacy. However, I can’t state this enough, it’s crucial to remember that Google is a search engine, and removal from search results does not equate to removal from the internet.
To further secure your online presence, consider utilizing the opt-out links provided in this article for various people search websites. These platforms can often inadvertently provide personal information that can be exploited by cybercriminals. By actively managing your online presence, you can significantly reduce your vulnerability to phishing and social engineering attacks.
Remember, cybersecurity is a shared responsibility. Stay informed, stay vigilant, and take control of your online presence to safeguard your personal information against potential threats.
___
Hello, I’m Jim Walker, The Hack Repair Guy – a veteran website security expert with over 20 years of experience in website hosting, security, and cleaning up hacked websites. As a trusted advisor to website owners and businesses worldwide, I provide website cleanup, management and protection services, and educational resources, to safeguard their online presence.My hands-on approach and expertise have helped thousands of clients recover from hacked websites and rebuild their online presence. I’m dedicated to making a positive impact in the website security industry, providing peace of mind and a secure online presence for everyone I work with. You can trust me, The Hack Repair Guy, to keep your website safe and secure. Please feel free to call or email me if you have any questions regarding website hosting or website security. I’m here to help!
Leave a Reply