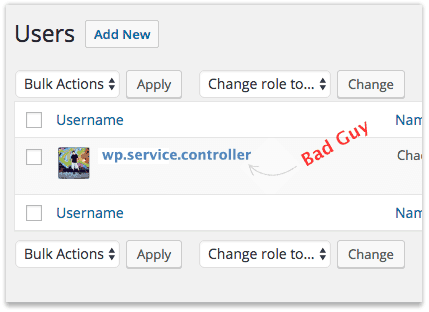
 If you reading this post, I suspect you’ve either been introduced to or met the WordPress user “wp.service.controller”
If you reading this post, I suspect you’ve either been introduced to or met the WordPress user “wp.service.controller”
Why the username wp.service.controller?
I’m not sure where hackers came up with this username of wp.service.controller. Well over 1 in 10 hacked websites I work on have this or a similar hacker administrator user added.
And in the years I’ve been securing websites that are infected with malware I’ve yet to find a common denominator or the common entry point used to add this malicious user account. In my experience, well over 80% of hacked websites are compromised through known exploits within outdated plugins or themes.
This post at WordPress.org summarizes the experiences of many in dealing with wp.service.controller user accounts.
How was the wp.service.controller WordPress user added?
At some point in the cybercriminals hacking process, the wp.service.controller user was set up in order to log into WordPress with the role of administrator.
Sadly, I often find wp.service.controller users added within websites previously cleaned by website malware cleanup companies. Suffice it to say, removing malware without taking the steps to properly secure a hacked website account will not stop hackers from returning and rehacking the website.
Administrator users may be added through exploitable plugins, installed PHP scripts or by using legitimate administrator logins. For this reason, it is important that you change your login passwords periodically, not use the same login password on multiple websites and do not use common passwords like “Password123”.
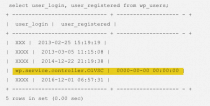 Website security tip: If the wp.service.controller user has a registration date of 0000-00-00 then it’s a near certainty that a PHP script was used to inject the wp.service.controller user account into your database. And if a PHP script was used to add hacker users, it’s imperative that you have a full malware scan or review done on your website as soon as you are able to do so.
Website security tip: If the wp.service.controller user has a registration date of 0000-00-00 then it’s a near certainty that a PHP script was used to inject the wp.service.controller user account into your database. And if a PHP script was used to add hacker users, it’s imperative that you have a full malware scan or review done on your website as soon as you are able to do so.
Remove wp.service.controller and then what?
Once you’ve removed the WordPress user accounts wp.service.controller or wp.service.controller.[random characters], be sure to remove all other not required user accounts as well.
I personally recommend not allowing more than one administrator account within a given WordPress website. If you have an editor or associate who needs to write or edit articles, the “Editor” role will suffice nicely.
[youtube https://www.youtube.com/watch?v=iAbE11H2Gbc&w=320&h=240&align=right&rel=0] If you are still using the administrator username “Admin” this would be a great time to add a new administrator account for yourself, log out as “Admin” and then log back into your more secure administrator account. Why give hackers half of the login puzzle?
Since your website was compromised, it may be worthwhile to consider how the hacker broke into your account and take measures to reduce the likelihood that your site will be compromised in the future.
To start, do you have more than a few WordPress websites sharing the same account?
The more websites you have sharing a single shared hosting account the more likely it is that you’ll be compromised again in future. I discuss this a bit more in my short post, “Are You A Cat Herder?” and in more detail in my article, “Why Shared Hosting Can Be Bad For The Health Of Your Web Design Business.”
Do you update your WordPress website and plugins at least monthly or do you have someone who can help monitor and update your WordPress website more frequently?
Updating WordPress regularly is the most effective preventative measure in keeping the hackers out of your website.
Enjoy!
1 Comment
For beginners and experts as well, this guide is useful for both because nowadays due to heavy hacking attacked, people need to secure their websites and your post is written accordingly.