Within the WordPress community, I find a lot of folks use a variety of security plugins and methods to secure their websites against denial of service attacks and brute force connections.
Recently I’ve begun reading several comments in the Facebook forums and personal blogs regarding how poorly Cloudflare performs against automated website attacks.
I find this strange because Cloudflare has always promoted the benefits of its distributed content delivery network (CDN) to help reduce the impacts of extreme events, like mass IP connections, and it has protocols in place to help reduce Layer 7 DOS and brute-force attacks as well.
That said, it’s become apparent to me that many are simply not taking the next step in using Cloudflare to better protect websites against denial of service attacks (video), and implementing them appropriate to their needs.
I use the free Cloudflare service to help protect my website and I use my web host’s free SSL certificate to better secure my login page and forms. Using the free Cloudflare and SSL certificate services seems like a no-brainer to me.
So what about blocking the bad guys and bad bots you ask?
If you have Cloudflare set up already, then you are halfway there. A little-known feature of Cloudflare, called “Advanced Rate Limiting” allows you to create rules to block specific types and rates of traffic connecting to your website. Best of all, the Advanced Rate Limiting service is free (with some limits).
Check this article, Introducing Advanced Rate Limiting on the Cloudflare website for more details.
Quick start:
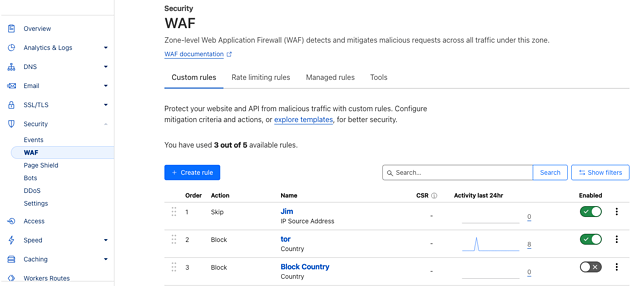
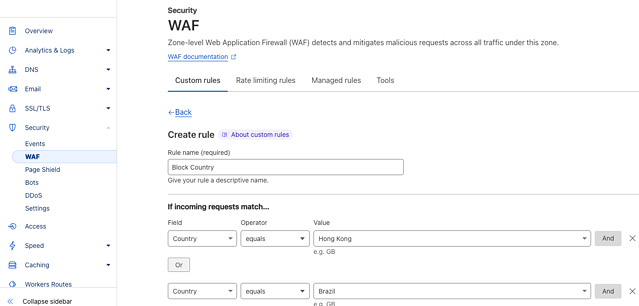
To get to the Advanced Rate Limiting feature, after logging into your Cloudflare account, see the Security -> WAF section (shown below):
The details…
To access and configure Advanced Rate Limiting in Cloudflare, follow these steps:
- Log into the Cloudflare Dashboard: Select your domain.
- Navigate to the Security Section: Once in the dashboard for your selected domain, click on the “Security” tab to access the WAF features.
- Access WAF and Rate Limiting Rules: Within the WAF section, look for the “Custom rules” option.
- Create or Modify Rate Limiting Rules: The new rate limiting rules allow you to combine different fields, similar to the functionality of WAF custom rules, offering more granular control over how you manage and mitigate traffic.
- Specify Rule Conditions and Actions: When creating a new rule, specify the conditions under which the rule should trigger. This could include the characteristics of the requests you want to limit or block, such as requests from a specific country. Then, choose the appropriate action, such as blocking the requests or applying a managed challenge.
- Review and Deploy: After configuring your rules, review them to ensure they meet your requirements, then deploy them.
Blocking countries is particularly easy to set up with custom rules (example below):
How can I test this?
This page on the Cloudflare website, Advanced Rate Limiting: Live Demo, provides a taste of what rules can be set, including a nice test page where you can see what happens when you visit/refresh a web page 10 times; a rate limit rule you might set for a login page: https://www.cloudflare.com/rate-limit-test
If you have experienced an increase in login attempts or attacks on your website I recommend trying out the Cloudflare Advanced Rate Limiting option to help control and block suspicious connections to your website.
What does it cost?
The free plan is rather limited rules-wise, but it does allow you to set up a few free rules to get started.
As far as I’m aware, in 2024, Advanced rate limiting is unmetered, meaning Cloudflare does not charge extra for Advanced Rate Limiting. Here’s a link to their website with more details on the cost of rate-limiting rules.
But what about Cloudflare Page Rules?
 Page rules were first promoted by Cloudflare back in 2012. As the name describes, Rules allow one to control how CloudFlare works on your site on a page-by-page basis.
Page rules were first promoted by Cloudflare back in 2012. As the name describes, Rules allow one to control how CloudFlare works on your site on a page-by-page basis.
Check out the article, “The future of Page Rules” which describes in more detail how the old page rules at Cloudflare have changed.
As of 2024, Cloudflare has since migrated the prior firewall rules into the new WAF custom rules noted above, which means that users who had previously set up firewall rules will now manage them as WAF custom rules.
Sadly, Cloudflare is rather cloudy on how to use the newly named features, so I recommend logging into your Cloudflare account and trying the varying options to figure out which works best for your website’s security needs.

I hope you’ve enjoyed this article and found it helpful. If you have any questions please feel free to call me anytime. I’m here to help.
About this article: I have no relation to Cloudflare and no content on this page is a paid for promotion.
 McAfee SiteAdvisor and McAfee WebAdvisor are two names for the same service. Originally known as SiteAdvisor, the service underwent a rebranding in 2017 and is now referred to as McAfee WebAdvisor. To dispel any confusion, this article will focus on the process of removing blocklist warnings from both services, which are fundamentally identical. I’ll use the service names McAfee SiteAdvisor and McAfee WebAdvisor interchangeably throughout this article, as many of McAfee’s internal links still use the original name. I know, it’s 2023… Right!
McAfee SiteAdvisor and McAfee WebAdvisor are two names for the same service. Originally known as SiteAdvisor, the service underwent a rebranding in 2017 and is now referred to as McAfee WebAdvisor. To dispel any confusion, this article will focus on the process of removing blocklist warnings from both services, which are fundamentally identical. I’ll use the service names McAfee SiteAdvisor and McAfee WebAdvisor interchangeably throughout this article, as many of McAfee’s internal links still use the original name. I know, it’s 2023… Right!
 Hello, I’m Jim Walker, The Hack Repair Guy – a veteran website security expert with over 20 years of experience in website hosting, security, and cleaning up hacked websites. As a trusted advisor to website owners and businesses worldwide, I provide website cleanup,
Hello, I’m Jim Walker, The Hack Repair Guy – a veteran website security expert with over 20 years of experience in website hosting, security, and cleaning up hacked websites. As a trusted advisor to website owners and businesses worldwide, I provide website cleanup,