HackRepair News – “Heartbleed” + OpenSSL + Hackers = Server Patching Mania
Just a quick note regarding the OpenSSL vulnerability, also known as "Heartbleed." An excerpt from the Heartbleed bug summary , "Bugs in the OpenSSL's implementation of the TLS/DTLS (transport layer security protocols) heartbeat extension (RFC6520). When it is exploited it leads to the leak of memory contents from the server to the client and from the client to the server." Without ...
HackRepair News – WordPress 3.8 update
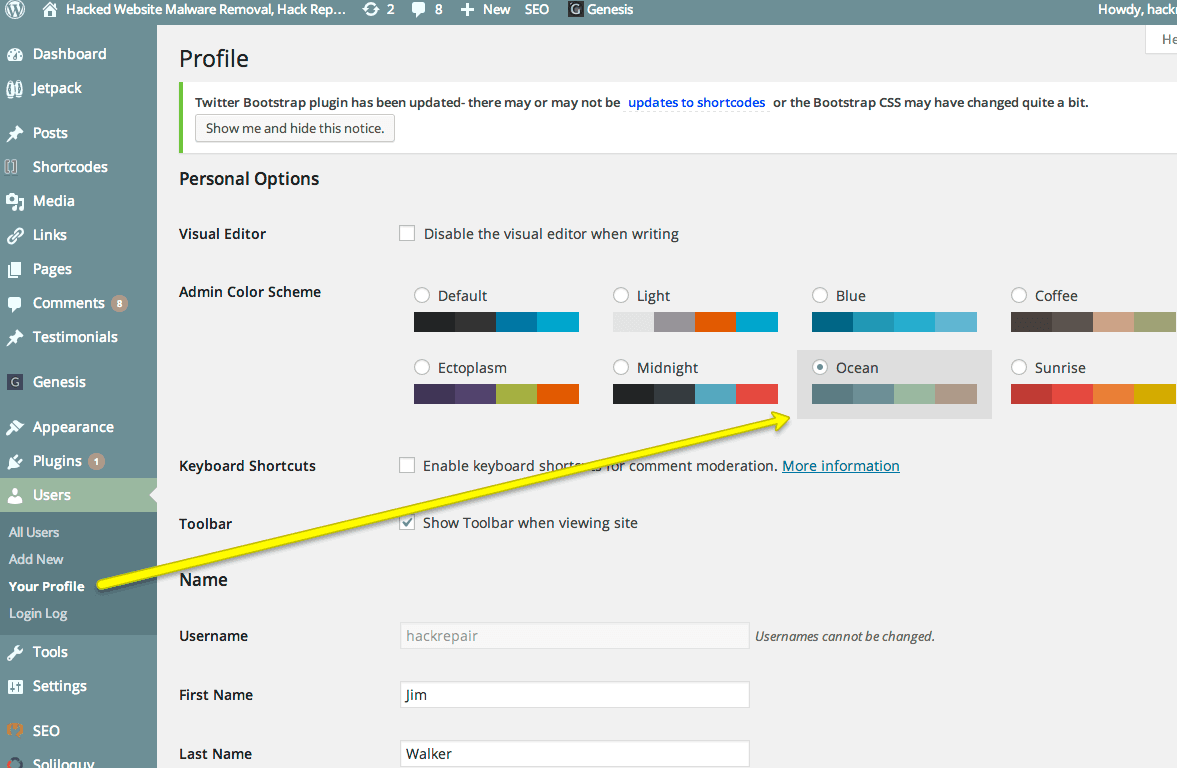
Just a quick note regarding the WordPress 3.8 release. You will see some big changes: Dashboard completely overhauled and more responsive. You may change the colors via: Users -> Your Profile. Other color schemes may be set up using this plugin, Admin Color Schemes New theme is greatly changed, with a more magazine like look and feel. Widget management has been improved ...

HackRepair News – “Heartbleed” + OpenSSL + Hackers = Server Patching Mania