HackRepair.com is dedicated to pro-active and re-active security. To keep our skills sharp, we attend the largest hacker conference on Earth, DEFCON 25, held for the last 25 years, in the heat of summer, at Caesar’s Palace, Las Vegas, NV USA.
For all but two of the last sixteen years, we’ve been sending our folks to DEFCON Las Vegas to learn as much as we can about the latest cyber attack and mitigation techniques.
DEFCON ran for four days this year.
Day 1 of DEFCON this year was full of new sights and sounds… Every few years, DEFCON outgrows its stomping grounds, and this happened in only 2 years at Paris/Ballys.
DEFCON is now at Caesar’s Palace!
This is the biggest DEFCON yet, and Caesar’s Palace is a gigantic maze, with many 10’s of thousands more square feet than last years venue.
The best part about the new location? Room elevators that go straight to the convention floor, and bigger aisles to route traffic!
DEFCON – Voting Machine Village
Every year now, DEFCON expands with a new ‘village’ that will focus on a single topic. This year it was voting machines, the same things we trust our very democracy with.
Voting is a sovereign right. But there have been issues with voting throughout history. Many recall the 2000 election, with hanging / pregnant chads making headlines for the ages. Since 2000, not as much weight has been given to the massively complicated electronic voting infrastructure that is employed in the United States.
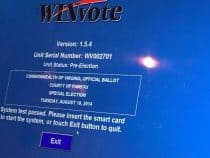
This year DEFCON brought over a dozen electronic voting machines, many still in use today, for hackers to crack, break, and bend to their will. It took less than 90 minutes before the first machine fell, and ultimately, every single one was compromised over the
It took less than 90 minutes before the first machine fell, and ultimately, every single one was compromised during the 3-day event. This research should inform voting machine companies, state and local governments, and the world, in how we need to move forward with securing our vote!
This research should inform voting machine companies, state and local governments, and the world, in how we need to move forward with securing our vote!
DEFCON 2017, Day 2-4 are where the real talks start, and where the most important talks start winding their way through to the weekend.
Some of our favorite talks this year at DEFCON 2017 were:
Day 2
° The Brain’s Last Stand (video below)
° Starting the Avalanche: Application DoS In Microservice Architectures

° Death By 1000 Installers; on macOS, it’s all broken!
° How We Created the First SHA-1 Collision and What it means For Hash Security
° Abusing Certificate Transparency Logs
° Cisco Catalyst Exploitation

Day 3
° Evading Next-Gen AV Using Artificial Intelligence
° Abusing Webhooks for Command and Control
° A Picture is Worth a Thousand Words, Literally: Deep Neural Networks for Social Stego
° Linux-Stack Based V2X Framework: All You Need to Hack Connected Vehicles
Day 4
° PEIMA (Probability Engine to Identify Malicious Activity): Using Power Laws to address Denial of Service Attacks
° The Call Is Coming From Inside the House! Are You Ready for the Next Evolution in DDoS Attacks?
° Malicious CDNs: Identifying Zbot Domains en Masse via SSL Certificates and Bipartite Graphs
° Friday the 13th: JSON attacks!
DEFCON 2017 – The Aftermath
Information Security is a tricky business. A lot of people talk about “white hat”, or “black hat”, sometimes even “grey hat” hackers. But in the end, some things that you find or you research can get you in trouble in ways that are complicated, and rarely understood.
A note on the least often discussed part of DEFCON. The aftermath of the talks, the events, and the mere presence of someone in the midst of thousands of like minded individuals in the middle of the desert. Marcus Hutchins, a security researcher from the UK was arrested by the FBI on his way back home from DEFCON, and has not been seen nor heard from since Wednesday the 2nd. You may or may not have heard of Marcus Hutchins, or MalwareTech back in May when he unexpectedly stopped the WannaCry Ransomware attack that spread through the night and early hours of May 12th, 2017, by simply registering a domain name that he found while researching the ransomware. Amazingly, this stopped the attack from spreading further.
You may or may not have heard of Marcus Hutchins, or MalwareTech back in May when he unexpectedly stopped the WannaCry Ransomware attack that spread through the night and early hours of May 12th, 2017, by simply registering a domain name that he found while researching the ransomware. Amazingly, this stopped the attack from spreading further.
Mr. Hutchins’ arrest is part of a long line of arrests in Las Vegas around DEFCON and Blackhat, and it will certainly not be the last. Apparently, he has been indicted on charges that he helped code, and distribute the Kronos banking trojan from 2014. But there is also evidence that he was simply researching it, asking for copies after the fact.
I’m sure you can see how the same people that appear to be helping, can also potentially be seen as harming. Whether these charges are founded or not, hackers and researchers, good and bad, will continue to flock to Vegas every summer.
Silencing security researchers, good or bad, through arrest, detainment, harassment or otherwise only makes the world less secure.
Understanding and utilizing the information gleaned from these talks is our bread and butter. Protecting your sites from attacks by malicious hackers is what we do.
“Secure By Default” is our philosophy and this is how we do it.
We’ll see you next year, at DEFCON 26!