“What’s a web shell?”
Most hacked websites have one or more web shell scripts added either during or after the site has been compromised.
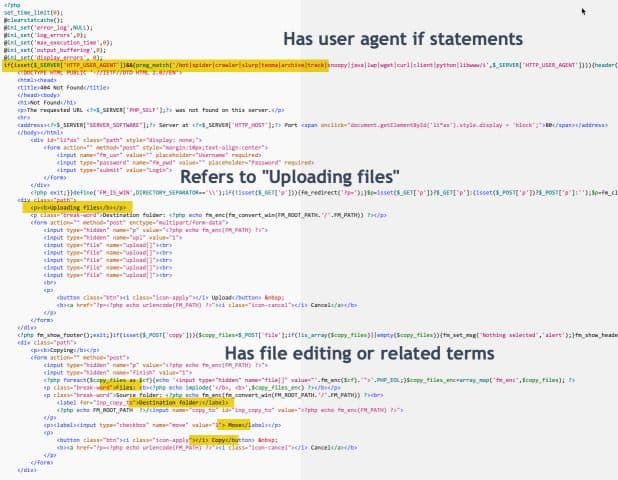
 Web shell scripts, sometimes called backdoor scripts, often include a visual interface that may be used to upload, rename, copy, move, or edit files. These scripts may likewise be used to view, edit, or download a website’s database.
Web shell scripts, sometimes called backdoor scripts, often include a visual interface that may be used to upload, rename, copy, move, or edit files. These scripts may likewise be used to view, edit, or download a website’s database.
Not all web shell or file manager scripts are malicious. A website designer may use these types of scripts legitimately to add administrator users to a WordPress website, edit theme files, or make website backups.
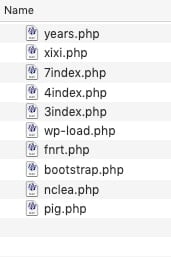
Backdoor scripts may be named anything, though, within a WordPress site, these types of scripts usually stand out from the core WordPress files. They may have file names like module.php, users.php, or have random letters like fnrt.php.
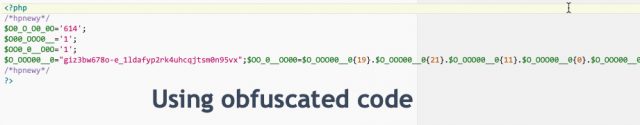
Below are examples of web shell scripting. Notice how some hacker scripts may be readable while others may be encoded or obfuscated? Either way, if a script’s code looks malicious, it probably is. Examples:


Why Is My Website Being Repeatedly Hacked?
Now that you have a better idea of what a web shell or backdoor script looks like, let’s discuss why your website might be repeatedly hacked.
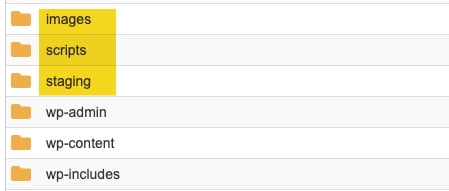
With respect to WordPress. Hackers are often quite good at hiding their malicious scripts in places you might not think to look. For example, I often find web shell scripts within image directories or other directories not associated with WordPress.
If you believe your site is compromised, be sure to check whether other directories have been added within your website hosting account, outside of the usual wp-admin and wp-content, and wp-includes directories. See the example at right.
Likewise, if you have more than one WordPress website installed within your hosting account, assume all are hacked. An analogy I like to use with new clients: “If a burglar breaks into your house, is he likely going to just hang out in your kitchen, eat all your cookies, and then leave?”
Just like the hiding of scripts within unassociated directories, I’ve seen hackers compromise a hosting account using known script exploits within one WordPress installation but leave that website remarkably unscathed malicious-scripting wise. Why? The hackers’ general hope is that you’ll leave the apparently unhacked website alone and only clean up the obviously hacked WordPress installation. This leaves the hacker an “open window” for future attacks.
![]()
Let’s summarize what I’ve covered here today. First, nearly all hacked websites will have web shell scripts installed. These scripts allow the hacker ongoing access to your hosting account. And second, be aware that a hacker rarely hides these backdoor scripts in plain site, so be sure to consider every directory within your account as a potential hiding place.
Enjoy!
Leave a Reply